Cyber criminals continue to target cash points (ATMs) causing significant loss to the banking and financial industry. They target the vulnerabilities and security flaws found in the outdated (and unpatched) operating systems still used in many Automated Teller Machines, stealing financial information and dispensing large amounts of unauthorised cash.
Anatoly Kazantsev, specialist threat researcher at Avira Protection Labs, recently found an ATM malware in the wild that specifically targets Wincor and Diebold ATM machines. Further investigation of these samples suggests that the campaigns originated from Portuguese-speaking countries.
In this blog, we will analyze the ATM malware samples that were recently found.
Malware sample analysis
SHA256: 7cea6510434f2c8f28c9dbada7973449bb1f844cfe589cdc103c9946c2673036
This sample uses CEN/XFS API to communicate with the ATM cash dispenser.
The CEN/XFS standard defines a common language to speak with the hardware components of the ATM. It shares a common conceptual background with Microsoft Windows device drivers. XFS stands for eXtension for Financial Services and has the following architecture:
 figure 1: XFS architecture
figure 1: XFS architecture
The ATM malware sample is written in C language and compiled using a MinGW GCC compiler as a 32-bit console application:

For further analysis, we upload the malware sample into IDA Pro and import MSXFS.dll library that implements XFS API functions:
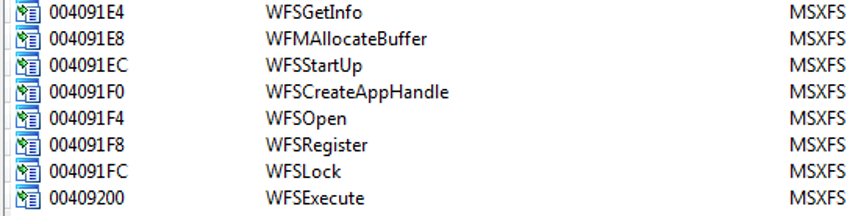
These functions are called from _main function. In general, the malware logic is straightforward and mostly implemented inside the _main function. The function is the biggest part of the sample’s executable code:
The function’s graph (a few if-else and switch-case constructions):

These if-else and switch-case constructions handle the return values and print error or information messages to a console. We will not describe _main function in detail, only concentrate on WFS* functions call and its parameters.
Now, let’s review a typical XFS API usage scenario and map malware’s behavior to this workflow:

As we can see from the import table, the malware doesn’t care about clean-up after itself. It only uses necessary functions (marked bold in the below table) to execute a specific command.
| Action | Function name | Description |
| StartUp | WFSStartUp | Connects to XFS Manager |
| Open | WFSOpen | Establishes a session between an application and the Service Provider |
| Register | WFSRegister | Enable monitoring of a class of service events by an application |
| Lock | WFSLock | Establish exclusive control by an application of a service |
| Execute | WFSExecute | Send service-specific commands to a Service Provider |
| Unlock | WFSUnlock | Release exclusive control by an application of a service |
| Deregister | WFSDeregister | Disable monitoring of a class of service events by an application |
| Close | WFSClose | Close a session between an application and the Service Provider |
| CleanUp | WFSCleanUp | Terminate a connection between an application and the XFS Manager |
Let’s take a closer at the most important functions to understand malware goals:
First, WFSOpen function takes its first argument the string “CDM30”:
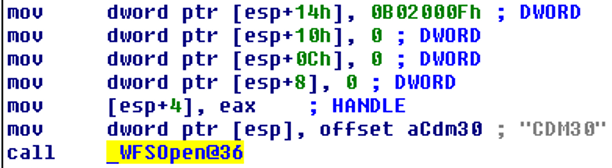
A quick Google search gives us the meaning of the string:

Now we know that this particular sample targets Wincor ATMs and establishes a session with Cash Dispenser Module (CDM) service provider.
The next interesting XFS API call is WFSExecute. This function takes 5 arguments. Two of them define command ID and command data – dwCommand and lpCmdData accordingly. In our case, dwCommand equals 302 and it is WFS_CMD_CDM_DISPENSE command ID:
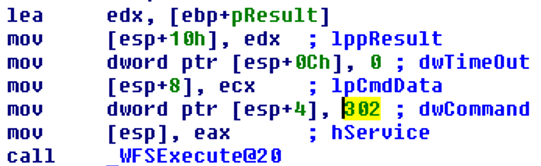
Command name describes itself – malware tries to dispense some cash. Amount and currency are defined in a special structure lpCmdData. Inside the _main function there are some interesting string:
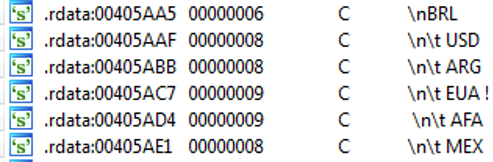
According to ISO4217 (https://en.wikipedia.org/wiki/ISO_4217):
- BRL – Brazilian real
- USD – United States dollar
- ARG – seems malware authors meant ARS (Argentine peso)
- EUA – Euro (EUR)?
- AFA – Afghan afghani (AFN)?
- MEX – seems malware authors meant MXN (Mexican peso)
If the malware didn’t find one of the above currency code, it will use a value returned by WFSGetInfo call.
To set an amount of money, malware fills a field of special structure (var_260) with value 1000:

After some manipulations this structure is passed as lpCmdData argument to WFSExecute function:

It is interesting to see that the first upload to VirusTotal originated from Brazil:

Similarly, the currency we saw earlier and strings in Portuguese tell us the malware targets Latin America countries (and possibly written by Portuguese-speaking attackers).

Conclusion
The results of the analysis indicate that the authors behind these attacks target Wincor and Diebold ATMs. We regularly see malware attacks on ATMs mostly because of un-addressed critical issues found in the systems. The detection and prevention of these kinds of threats can be done in multiple ways, and is made easier because the focus of the malware is on executing some specific commands and doesn’t clean-up after itself. Avira’s range of detection mechanisms protects its customers from such attacks; powerful machine learning based anti-malware technologies help to extend the security level of ATMs and provide protection from known, unknown and advanced threats.
IOCs
5c002870698258535d839d30f15c58934869c337add65c9b499aca93fb1c8692
7cea6510434f2c8f28c9dbada7973449bb1f844cfe589cdc103c9946c2673036














Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.