Two days ago, the Avira Virus Lab noticed a new wave of Locky ransomware targeting our users. This is a typical file encryptor that will make your precious files (e.g. photos, documents) unreadable and it will oblige you to pay a ransom in exchange for the decryption key.
The bad news
This new wave is being spread through Office Word documents, not only Microsoft but also other programs such as Libre Office, which look like the following image:
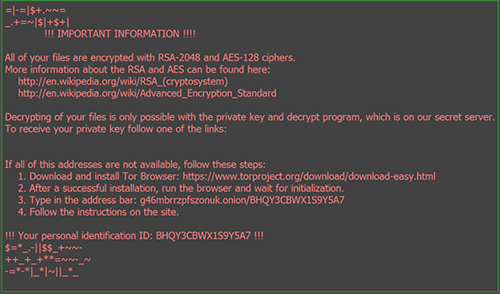
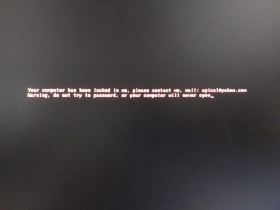
The malware author tricks the user into double-clicking the envelope. By doing so, this sets off a cascade of actions which will end in all valuable files being encrypted and the user getting the following message.
This encryption method changes the file extension into “.asasin” and multiple other files with payment details have been written onto the disk.
The good news
Avira’s artificial intelligence system detects these kinds of threats from the first moment they were seen on our clients’ computers and a message from our antivirus will pop up stating that a HEUR/APC threat was found. In addition, we also delivered a signature named ”TR/Locky” to our clients via the updates mechanism.
Related article
https://blog.avira.com/ransomware-attacks-not-victim/
Some technical details
Behind this image from the word document, there is a LNK file also known as a shortcut in windows. Dumping the file to disc enables us to see what its intentions are.
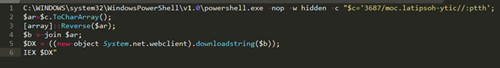
By pasting the command into a text editor, we can clearly see that this shortcut is meant to run a PowerShell script:
The script is in clear text and can easily be read. Its intent is to download another PowerShell script from a link embedded in the script and then run this script by using the Invoke-Expression function.
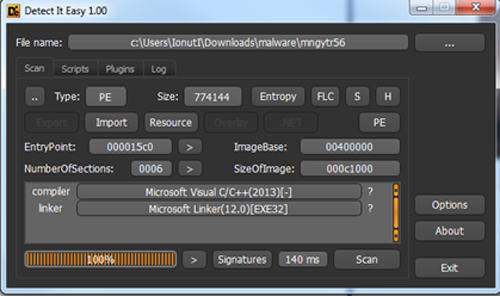
This second script will connect to the internet and download a Windows executable file to the %temp% folder with the “losos1.exe” name and instantiate a process from it. This executable is compiled with Microsoft VC 2013 and also contains multiple stages of code obfuscation to confuse analysts and trick people into thinking it’s a clean file.
Multiple useless strings can be observed in the following image along with the “system32\calc.exe”
There is some misleading information built into the executable that can trick the user into thinking this is a legitimate Microsoft application:
After the new process has been created, it copies itself as “svchost.exe” and creates a new instance of it and deletes the first executable:
Checks the following mutex to verify if it’s already running on the system:
- “Global\Ca4a2aDa1aGaFa3a9aGa3a9aBa9a:aCa”
Gathers information about the operating system and sends it encrypted to the C&C server as follows with the scope of retrieving an encryption key:
- Param: id=[..]&act=getkey&affid=[..]&lang=en&corp=0&serv=0&os=Windows+7&sp=1&x64=1&v=2
- user-agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E)
Reference samples:
e49c6973ddcc601cfb85b451e122903b1a9c036c8baafc35cb327f76b998c537
423dc1aaaed311349f9932a643a032d18f0589b97275b501a7a7f6955f5aac46
While Locky works hard to avoid detection, but that is not enough. Avira Antivirus detects Locky on several layers within its cloud detection.
This post is also available in: Italian