Our malware threat report for Q1 2020 highlighted cyber threats and exploits that included, phishing and malspam campaigns, and a surge in Emotet related attacks. This midyear malware threat report provides more in-depth insight into sophisticated attacks including, PE (Portable Executable) and non-PE threat categories, Android and macOS threats. We’ll also take a closer look at growing Office attacks and IoT malware observed by the Avira Protection Labs.
Threat Summary

PE Malware Threats
In Q2 2020, we saw a very small reduction in total detection events. This overall reduction in detection events can be attributed to malware authors shifting from volume to more complex and sophisticated attack methodologies, leveraging MS Office, and script-based threats. Although mobile devices faced fewer attacks compared to Q1 2020, Adware and PUA continue to grow.
PE or ‘Portable Executable’ is commonly used to describe binary executables within the Windows OS. PE includes ‘.exe‘ and ‘.dll‘ file-types and less well-known formats such as ‘.scr‘. They are by far the most used data structure for malware attacks on the Windows platform.
In general, the mix of malware categories is quite stable, with trojans most often seen followed by file infectors.
 Figure 1: PE detection categories in Q2, excluding Heuristic detections
Figure 1: PE detection categories in Q2, excluding Heuristic detections
The Ramnit, Sality and Virut families of PE file infectors are most commonly identified by our machine learning enabled heuristic systems. File infectors are noteworthy here. Due to their nature of possibly infecting hundreds to thousands of files per computer, they can generate a lot of unique detection events.
 Figure 2: Top 10 PE detections in Q2
Figure 2: Top 10 PE detections in Q2
Ramnit
In 2019, Ramnit was among the top malware families causing financial attacks. The Ramnit malware family steals confidential data from infected machines or, depending on the variant, includes a botnet capability. It spreads through .exe, .dll, or HTML files.
Sality
Previously, it appeared to be a worm, but now the Sality malware family acts as a backdoor connecting infected machines to a botnet. It is most commonly distributed through .exe files. Recent variants can communicate through the P2P network.
Virut
Virut belongs to a polymorphic malware family and spreads through .exe files. It possesses entry-point obscuring capabilities, including IRC backdoor.
Non-PE Malware Threats
Non-PE threats, as the name suggests, are not Windows executables, but other means of infecting machines. In this category, we have Office files, scripts, PDFs, and other exploits.
Q2 2020 saw many more people from home as a result of the pandemic. Malware authors and bad actors have recognized the opportunity presented by users working outside the office and have adapted their attacks appropriately. In this quarter, we observed not only a surge in Non-PE samples in the wild but also an increase in (prevented) attacks on our customer base. We saw a significant rise in script-based detections (73.55%) and Office based macro detections (30.43%).
 Figure 3: Logarithmic view of NonPE detection categories in Q2
Figure 3: Logarithmic view of NonPE detection categories in Q2
We can also saw a month-to-month trend away from PDFs and a surge in JavaScript attacks.
When we take an in-depth into the top 10 NonPE threats, we observe the same trend. Office and Web-based detections hold the top positions:
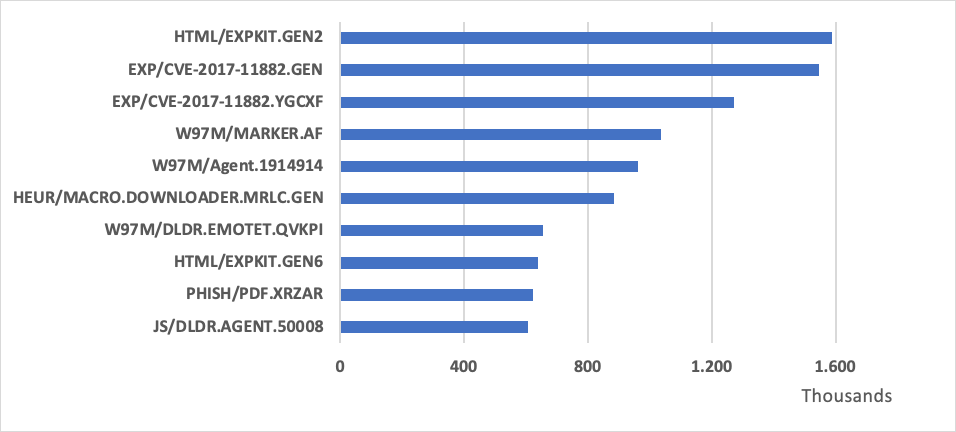 Figure 4: Top 10 NonPE detections in Q2
Figure 4: Top 10 NonPE detections in Q2
W97M/Marker
One of the most prevalent malware families in the Office documents category was W97M/Marker malware. W97M/Marker infects other documents by appending the malicious code to the existing macro code. The name comes from the “you are marked” text comments used to locate the beginning of the code.
CVE-2017-11882 Exploit
In Q2 2020, Avira telemetry showed a lot of Office threats that are using an old stack buffer overflow vulnerability in Microsoft Equation Editor, CVE-2017-11882. This enables remote code execution and downloads the malicious payload.
Documents containing Excel 4.0 Macros
By far, the most significant increase has been observed in Office documents using Excel 4.0 or XLM macros techniques. It gained popularity among malware authors over the last year. As shown in the figure below, the peak was in May, followed by a decreasing trend in June.
Briefly, this is an ancient and well-known technique, but this new campaign made use of a few tricks to confuse users. Some of them were using the hidden or very hidden properties to camouflage the sheets which were containing the macro code, and others were password protected.
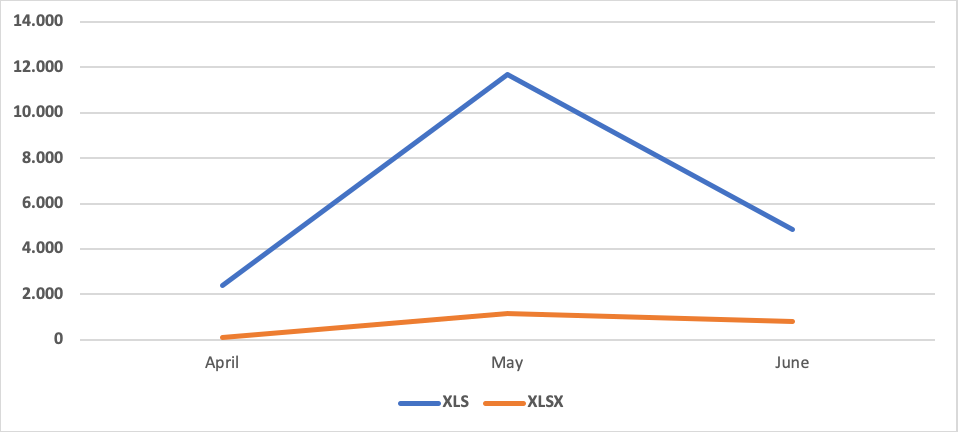 Figure 5: New incoming Excel samples based on version
Figure 5: New incoming Excel samples based on version
Office documents spreading Zloader and Dridex malware threats
Zloader and Dridex are well-known banking malware. They aim to steal credentials and other types of private information from targeted users. In Q2 2020, the primary infection vector was COVID-19 themed e-mails containing Office or PDF files, which further assisted the download of the malicious payload.
Android Malware Threats
The global Android threat activity has toned down a bit this quarter, compared to the previous one. The first two months show a slight increase in detections compared to their respective months in the last quarter, with June being noticeably below March.
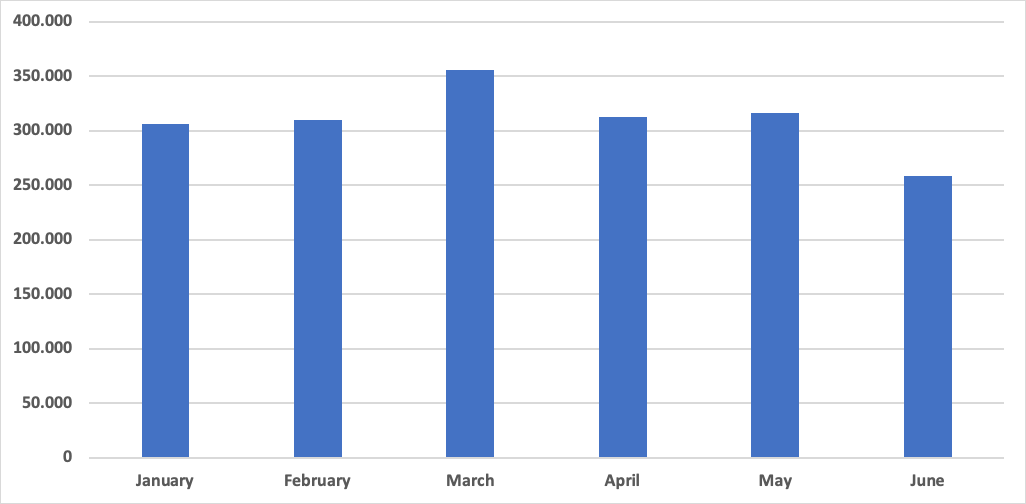 Figure 6: The Android threat activity in Q2 compared to Q1
Figure 6: The Android threat activity in Q2 compared to Q1
Android threats are divided into four different categories. Malware, which accounts for about ¾ of all our Android detections. Adware and PUA, which are a common sight in the mobile threat landscape, and Riskware.
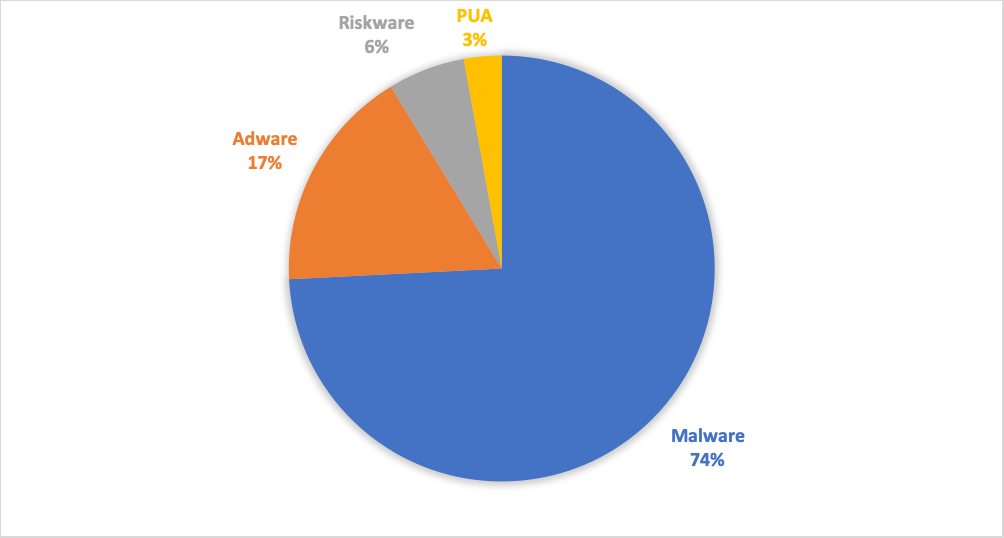 Figure 7: Android Threat Categories in 2020 Q2
Figure 7: Android Threat Categories in 2020 Q2
Out of the top ten detected families, five of them have intrusive advertisement display capabilities, with Android/Hiddad being the first one on the list. It is worth mentioning that “droppers” make up a third of the top ten detected families this quarter.
 Figure 8: Top ten detected families in Q2
Figure 8: Top ten detected families in Q2
Android/Hiddad
Applications containing Hiddad, an ad-distributing malware for Android, receive many 5-star ratings from infected users – unfortunately, not for the right reasons. Hiddad spreads as a YouTube downloading app. It usually goes to the market on Google Play labeled as Tube mate or Snap Tube.
Android/Dropper
An application detected as Dropper contains additional malicious apps within their payload to infect devices. They install the malicious component in the second stage of the infection cycle.
Android/SMSREG
An application detected as SMSREG shows malicious behavior for SMS/MMS. It steals text messages (potentially used to steal two-factor authentication codes) or send text messages to premium numbers, financially damaging the victim and obtaining money. On the global threat heat map, we can see that a high number of infections were detected and prevented in North African and South Asian countries. Iran especially saw over 3.000 attacks per 10.000 customers in Q2 2020.
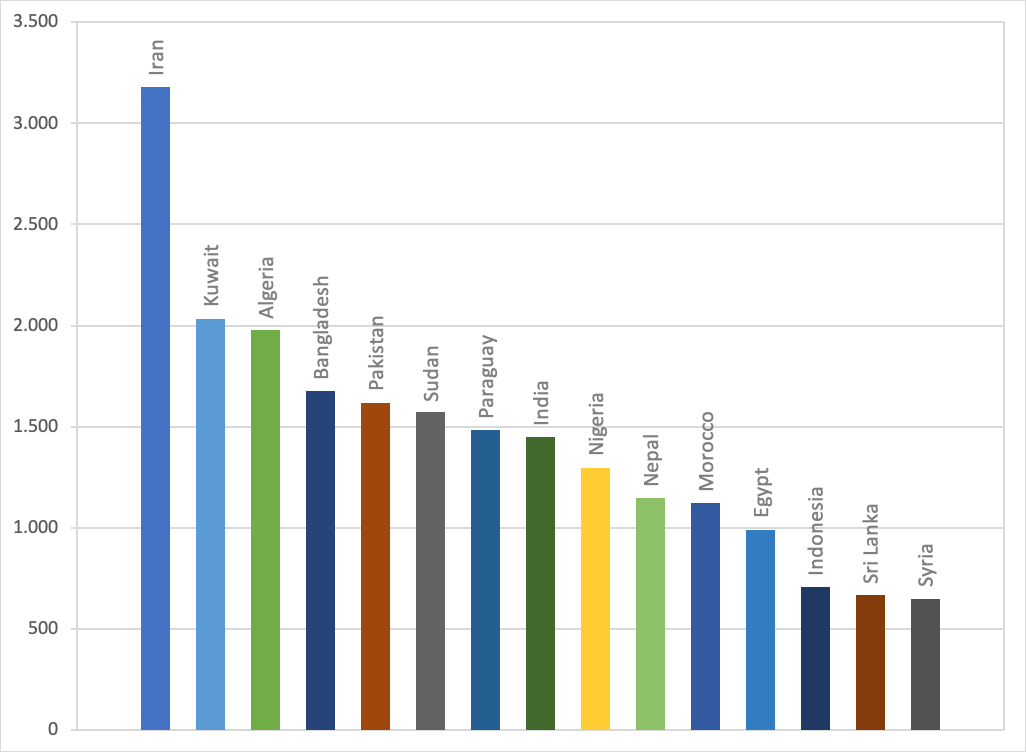 Figure 9: Android Detections per 10.000 users per country in Q2, excluding countries with less than 1.000 detections per quarter
Figure 9: Android Detections per 10.000 users per country in Q2, excluding countries with less than 1.000 detections per quarter
The European average ranks lower, Romania being the most attacked member-state with 436 attacks per 10.000 customers. Other notable countries: USA/France (117), Italy (109), United Kingdom (100), Germany (71), Canada (65).
The previous quarter saw a full-force attack of the COVID-19 pandemic that left its mark on the Android ecosystem. Malware authors exploited this chaos along with the Android users’ need for information and protection.
All types of malware, ranging from spyware and adware to more sophisticated banking trojans and SMS stealers, were distributed under the flag of COVID-19 related apps. Earlier, we analyzed the infection cycle of the Cerberus banking trojan.
 Figure 10: COVID-19 themed Android malware
Figure 10: COVID-19 themed Android malware
macOS Malware Threats
While people still believe macOS is untouched by malware, the Apple system often faces Office and script-based attacks, including Adware threats.
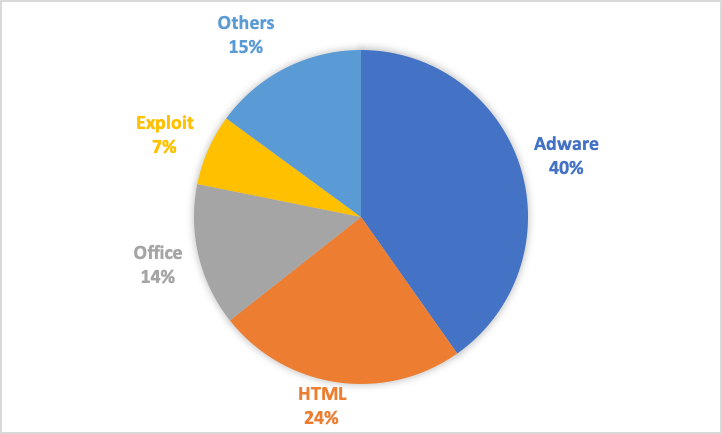 Figure 11: macOS Threat Categories in 2020 Q2
Figure 11: macOS Threat Categories in 2020 Q2
In the pie chart above, we see a mix of threat that Apple devices encounter. When it comes to a threat category, Adware is at the top of the list, followed by HTML (detects files able to infect the system using an HTML script), Office (malware ready to infect the system using tricks such as macros and VBA scripts inside the Office file), and Exploit (these files exploit vulnerabilities present in the targeted system or specific applications installed on it). The Other category includes malicious files detected as macOS (malware using macOS specific binaries), files using fake or hidden file extensions, phishing, and PUA.
Taking a look at the top prevalent threats infecting in the macOS environment, we can say that ADWARE/OSX.Surfbuyer, is one of four Adware applications in the top 10.
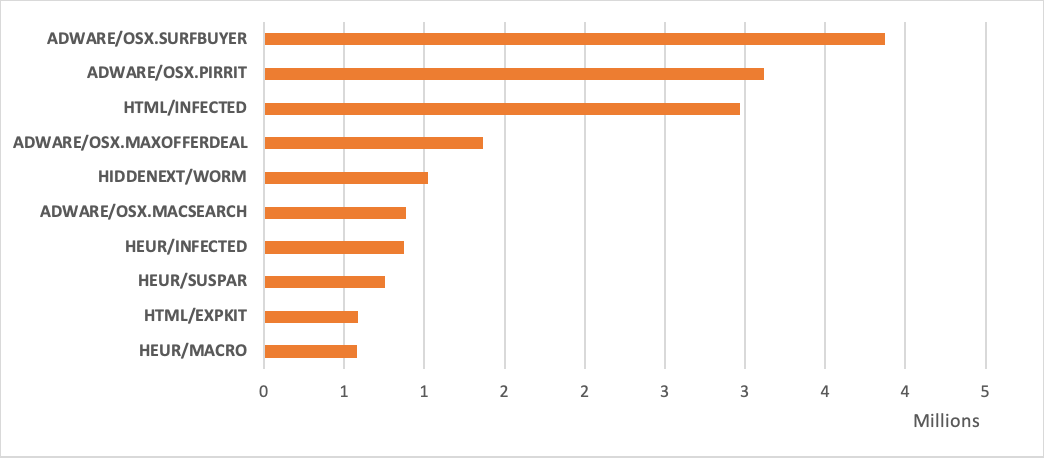 Figure 12: Top ten detected macOS families in Q2
Figure 12: Top ten detected macOS families in Q2
ADWARE/OSX.SURFBUYER
ADWARE/OSX.SURFBUYER are rogue applications claiming to save time and money by notifying the users of exclusive deals or discounts available on different internet shops. Their real behavior includes displaying intrusive online ads and tracking internet traffic.
ADWARE/OSX.PIRRIT
This detection is very similar to the one above, showing almost the same behavior, such as displaying intrusive ads, gathering data, and tracking internet traffic.
HTML/INFECTED
This family contains generically detected web pages showing malicious behavior.
IoT Malware Threats
In the IoT landscape, we observed the usual Mirai, Gafgyt, and Hajime as the top 3 IoT malware families. Different variants of these malware families comprised up to 85% of the IoT threat landscape.
In total, we saw about 20% more IoT related samples in Q2 compared to Q1. However, we saw a big wave of samples in March.
 Figure 13: The incoming IoT threats in Q2 compared to Q1
Figure 13: The incoming IoT threats in Q2 compared to Q1
Comparing three main threats shows us that Mirai remains the IoT threat of choice for smart device targeted attacks.
 Figure 14: Top three IoT families in Q2
Figure 14: Top three IoT families in Q2
Mirai
We’ve previously looked at how Mirai, an IoT botnet, has changed since its source code became public, and recent analysis of IoT attacks and malware trends show that Mirai has continued its evolution. The result is an increase in attacks, using Mirai variants, as unskilled attackers create malicious botnets with relative ease.
Gafgyt
Gafgyt malware first appeared in 2014. It started to exploit the known vulnerabilities in IoT devices, especially routers to launch DDoS attacks like Mirai. Gafgyt’s famous variants are BASHLITE and Qbot. Each variant serves its purpose. The malware uses a scanner function usually to find open nodes facing the internet before exploiting vulnerabilities. It also kills other botnet families if found on devices.
Hajime
Hajime appeared in late 2016. It belongs to the botnet family. It has a propagation module that makes it an advanced and stealthy family that uses different techniques like brute-force attacks on device passwords to infect devices, and then takes several steps to conceal itself from the compromised victim. Thus, the device becomes part of the botnet. After that, it includes an attacking module to serve the purpose. Hajime is built on a peer-to-peer network for its C&C servers, unlike Mirai, which contains hardcoded C&C servers addresses.














Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.