Welcome to our Q3 2020 Malware Threat Report.
Our previous malware threat report for Q2 2020 highlighted how malware authors shift from volume to more complex and sophisticated attack methodologies, leveraging MS Office, and script-based threats. This quarters’ edition provides more in-depth insight into sophisticated attacks including, PE (Portable Executable) and Non-PE threat categories, Android and macOS threats. We’ll also take a closer look at growing traditional malware attacks and new IoT malware variants detected by the Avira Protection Labs.
Threat Summary

In our Q3 malware threat report, we see similar trends overall to Q2 2020. While the overall detection number has not changed dramatically, we see a shift in how this number is put together.
We identified a significant rise of up to 50% in the number of traditional malware, exploit based threats, and coinminer. However, the adware/PUA, mobile, and script-based threats see a decline compared to the last quarter. General malware attacks surged and this category contains the most dangerous threats found in the wild. In this report, we will discuss each threat category in detail and look at their most common forms.
PE Malware Threats
Portable Executable (or PE) is commonly used to describe binary executables within the Windows OS. PE files include .exe, .dll, and .scr, and are the most commonly leveraged data structures in malware attacks.
In Q3 2020, PE malware represented the largest category of detected threats. Within this category, we see that the vast majority of attacks can be attributed to trojans and file infectors, PUA, and adware.
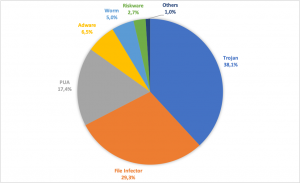 Figure 1: PE detection categories in Q3
Figure 1: PE detection categories in Q3
The chart below shows that threats have increased their attack-volume, quarter-on-quarter. The Fareit trojan saw over 80 times more detections in Q3 compared to Q2. Note that we excluded threats with a volume of less than 2.500 in Q2.
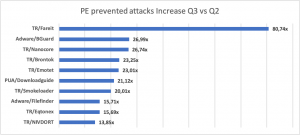 Figure 2: PE prevented attacks
Figure 2: PE prevented attacks
Fareit
Fareit is one of the most successful information stealers deployed in malspam campaigns. This family of trojans steal sensitive information such as website passwords and sends them to its backend servers. In 2020, it has been a continuous threat to the public health sector. It has also been associated with CVE-2017-11882, which is the top 10 most exploited vulnerabilities. Fareit usually steals info from:
- FTP clients
- Cloud storage services
- Browsers
- Mail clients
bGuard
bGuard is an infamous browser hijacker. It is an ad-supported (seen as banners, search results, pop-ups, pop-unders, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer, Firefox & Chrome. bGuard is mainly distributed through monetization platforms during installation.
It is usually bundled within the custom installer on various download portals, and generates traffic, displays ads & sponsored links. Some variants can also collect user-specific information with or without the user’s consent.
Nanocore
Nanocore is a RAT (Remote Access Trojan) that gives unauthorized access to a victim’s device. This RAT comes with a plugin mechanism to expand its functionality by developing additional features for other malicious actions. Major plugins include:
- Spying plugin: allows spying over the microphone and webcam access.
- Control plugin: allows better control over the compromised host having a range of tools.
- Security plugin: provides access to the compromised host’s AV tools and firewall to bypass them.
A newer version of Nanocore is more dangerous because of its advanced malicious features. There is an increase in the Nanocore activity, along with spam and phishing attacks associated with it.
Brontok
Brontok is a family of mass-mailing e-mail malware. It spreads by sending a copy of itself as an attachment to e-mail addresses that it gathers from files on the infected system. It can also copy itself to detachable pen drives.
Emotet
Emotet is considered to be the world’s largest malware botnet. Historically, the Emotet spam botnet has been linked to the distribution of banking trojans. Nowadays, it spreads spam to infect computers, including ransomware.
Recently, the Emotet net is dropping Trickbot to deliver ransomware and the Qakbot Trojan to steal banking credentials. It can hijack email chains to infect more users. Emotet also spreads with worm-like features via phishing email attachments or links that load a phishing attachment.
Non-PE Malware Threats
Non-PE threats, as the name suggests, are not Windows executables but other means of infecting machines. In this category, we have Office files, scripts, PDFs, and other exploits.
In the graph below, we can see the distribution of the common attack types for Non-PE. We observed fewer attacks than average in July in nearly every category. However, during August and September, the number of detections increased, leveling out the total average for the Q3 malware threat report.
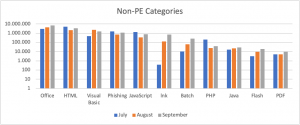 Figure 3: Non-PE detection categories in Q3
Figure 3: Non-PE detection categories in Q3
Non-PE Threat – Emotet
Now let’s take a closer look at the most impactful malware we have seen in 2020. Emotet has been very strong this quarter, as seen in the graph below. In July, we received a little over 5.000 documents distributing the Emotet payload. The number increased by around 41% in August and 127% in September to over 12.000, indicating continued growth.
 Figure 4: Office samples distributed by Emotet in Q3
Figure 4: Office samples distributed by Emotet in Q3
The malware distribution techniques are not very different, as seen in previous waves. Emotet uses obfuscated VBA code to connect to the URL to download the malicious payload. The first step in the infection flow is the e-mail message using social engineering techniques to camouflage the attached document’s malicious intent (below is an example).
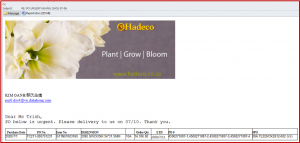
Figure 5: Example of social engineering
Non-PE Threats – Encrypted documents
In our last quarter report, we highlighted the comeback of an old technique using XLM macros. More recently, we’ve seen an influx of encrypted XF documents. In the chart below, we have included projections for October.
 Figure 6: Encrypted malware documents in Q3
Figure 6: Encrypted malware documents in Q3
Non-PE Threats – Other developments
- Maldoc campaigns distributing ZLoader malware were quite prevalent this quarter. The techniques used were as usual ones (XF documents, sometimes encrypted). The documents represent the first step in the infection flow, followed by a downloader VB script.
- Maldoc campaigns distributing QakBot malware were also detected this quarter. The documents used an excel formula to download fake png files (actually “.exe” files) from different URLs.
- New Ursnif malware campaigns were also distributed via Office documents. For this malware family, the infection flow consists of macro VBA documents.
Android Malware Threats
The global Android threat activity has reduced slightly in this quarter’s malware threat report.
 Figure 7: Android malware detections in Q3
Figure 7: Android malware detections in Q3
The general Android malware category is most common, followed by adware, riskware, and PUA. Other categories contain mostly heuristic & generic detections.
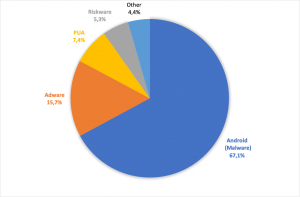 Figure 8: Android malware categories detected in Q3
Figure 8: Android malware categories detected in Q3
Out of the top ten Android families detected this quarter, four of them have the capability to display intrusive advertisements, with Android/Hiddad being the largest. It is worth noting that PUA makes the top five, and Android Lockers had a considerable presence in Q3.
 Figure 9: Top 10 Android malware families detected in Q3
Figure 9: Top 10 Android malware families detected in Q3
ANDROID/HIDDAD
The applications containing Hiddad, an ad-distributing malware for Android, received several 5-star ratings from infected users. Unfortunately, not for the right reasons. Hiddad is often presented as a YouTube downloading app. It usually goes to the market on Google Play labeled as Tube mate or Snap Tube.
ANDROID/DROPPER
The applications detected as Droppers contain additional malicious apps within their payload. Droppers install the malicious payload on the infected device and, in most cases, run it automatically. Droppers are used in the second stage of the infection strategy (installing the real malicious component).
ANDROID/SMSREG
The applications detected as SMSREG display malicious behavior regarding SMS/MMS, including stealing text messages (potentially used to steal two-factor authentication codes) or sending a text message to premium numbers, financially damaging the victim.
ANDROID/AGENT
This generic detection covers any malicious behavior that cannot be accurately classified into a specific category.
On the global threat heat map, the most attacked countries were Germany, Iran, Brazil, India, and Indonesia, each with over 35.000 detection events. Compared to the previous quarter, the United States has advanced a few positions, now being in sixth place.
 Figure 10: Top 10 attacked countries in Q3
Figure 10: Top 10 attacked countries in Q3
macOS Malware Threats
When it comes to threats prevented on macOS, our Q3 malware threat report shows that adware beats other categories. Adware is followed by script (includes JavaScript, PHP, HTML), Office (includes malware associated with Word, Excel, and PowerPoint), and exploits (malicious applications that exploit vulnerabilities in the system or in certain installed programs).
The ‘other’ category constitutes the remaining 35%. It includes HiddenEXT (a file that contains a malicious executable but it’s hidden by a harmless extension), phishing (a file that under false claims tries to persuade the user, for instance, to reveal personal information), and other types of detections such as Windows files that found their way into macOS environments.
 Figure 11: macOS threat categories detected in Q3
Figure 11: macOS threat categories detected in Q3
Now, let’s take a look at the prevalent threats infecting the macOS environment between Q2 and Q3. In this chart below, we omitted detections with less than 1.000 total detections in both quarters combined to eliminate low volume outliners.
 Figure 12: macOS prevented attacks quarter comparison
Figure 12: macOS prevented attacks quarter comparison
OSX/Filecoder
This detection covers a file-encrypting ransomware family. It uses torrent websites as its infection vector and disguised as a crack for certain applications, such as Adobe Premiere or Microsoft Office.
OSX/Flashback
This is a trojan family disguised as an installer for Adobe Flash Player, named “Flashback”. During installation, the malware will de-active network security features and install a dynamic loader library to inject code into the user’s applications. It was observed that the goal of this trojan is to form a botnet, which can be used for further malicious purposes.
OSX/Spynion
This detection covers a trojan family. It is distributed via several free macOS applications that, during installation, download and drop a malicious component on the user’s personal computer. The component is responsible for monitoring the user’s activity and sends confidential data back to the attacker’s servers. Some variants also have backdoor functionality, allowing an attacker to connect to the user’s personal computer remotely.
Adware/OSX.Tapufind
This malware’s behavior is a combination of adware and browser hijackers. It displays misleading advertisements in the victim’s web browser. It forwards the traffic to its landing pages (these include “search.tapufind.com” and “tab.tapufind.com”, the first one replacing the user’s search engine). This adware causes privacy issues for the user because it tracks internet activity. This type of malware comes via installation bundles, spam, or Fake Adobe Flash Players updates.
OSX/Zipcloud
This is an Unwanted Application (PUA) that claims to find discounts for cloud storage. It displays intrusive advertisements to the user and may steal personal data such as IP addresses and search queries. It comes via fake-free applications or installation bundles.
Looking at the threat heat map for OSX malware, we can see that OSX attacks are much more likely to occur in Europe and North America, with the most attacked countries being from these regions. Germany and the U.S alone make up for more than 50% of all registered macOS detections.
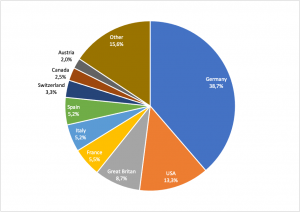 Figure 13: macOS Threat Categories in Q3
Figure 13: macOS Threat Categories in Q3
IoT Malware Threats
In the IoT landscape, we observed the usual Mirai, Gafgyt, and Hajime as the top 3 IoT malware families. However, Gafgyt has significantly increased its presence compared to the previous quarter.
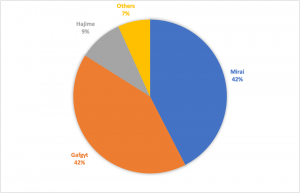 Figure 14: Top three IoT families in Q3
Figure 14: Top three IoT families in Q3
Mirai
We’ve often looked at how Mirai has changed since its source code became public, and recent analysis of IoT attacks and malware trends show that Mirai has continues its evolution. The result is an increase in attacks using Mirai variants, as unskilled attackers create malicious botnets with relative ease.
Gafgyt
Gafgyt malware first appeared in 2014. It started to exploit the known vulnerabilities in IoT devices, especially routers, to launch DDoS attacks like Mirai. Gafgyt’s famous variants are BASHLITE and Qbot. Each variant serves its purpose. The malware uses a scanner function usually to find open nodes facing the internet before exploiting vulnerabilities. It also kills other botnet families if found on devices.
Hajime
Hajime appeared in late 2016 and is a botnet family. It has a propagation module that makes it an advanced and stealthy family that uses different techniques like brute-force attacks on device passwords to infect systems. It then takes several steps to conceal itself from the compromised victim. Thus, the device becomes part of the botnet. After that, it includes an attacking module to serve the purpose. Hajime is built on a peer-to-peer network for its C&C servers, unlike Mirai, which contains hardcoded C&C servers addresses.
Diving deeper, let’s look at the sub-families and behavior categorizations in IoT. With our dynamic IoT detection module, we can find new malware or malware families variants based on their behavior. As shown below, we have captured quite new malware families/variants through this module in Q3 2020.
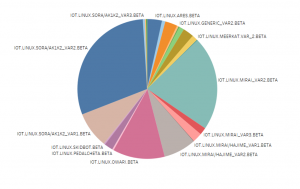 Figure 15: New IoT families detected in Q3
Figure 15: New IoT families detected in Q3
SORA
A Mirai variant that targets video surveillance storage systems. They use default password attacks plus exploit scanners.
OWARI
A Mirai variant targeting video surveillance storage systems. It tries to brute-force access using default password attacks and exploits scanners. OWARI and SORA were created by the same author.
SKIDBOT
It uses RCE vulnerability exploits & launches DDoS attacks.
ARES
It infects Android-based set-top-boxes (STBs).
IoT threats can also be categorized based on their network traffic. By design, IoT devices are very connectivity bound, so their traffic can tell you a lot about their purpose. This detection layer really helps in finding new exploits. By analyzing the traffic, we quickly detect attempted security exploitations. The notable exploits seen in this quarter are:
- UPnp SOAP Command Execution
- RCE Huawei
- Netgear httpd
- ZYXEL RCE
- Tenda RCE
- GPON RCE
- Aruba ClassPass Policy Manager
The network layer module also helps us detect malware families based on network or Command & Control communication behavior. For example:
- HAKAI
- AISURU
- YAKUZA
- SCYLLA
They have all distinct ways of communicating with their Command & Control infrastructure.
 Further reading
Further reading
In our mid-2020 vulnerability update, we leveraged the expert insight of Avira’s Vulnerability Detection Team – part of Avira’s Protection Labs – to look at some of the most critical vulnerabilities that could be exploited.
Learn more about new and novel malware, or automatically receive our Q4 malware threat report by subscribing to Avira Insights blog’s research section. Visit oem.avira.com to out how you can improve your own detection rates by using Avira’s anti-malware SDKs or threat intelligence.
Learn how to build your own security solutions with our anti-malware SDKs and threat intelligence














Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.