This time, it’s not just EternalBlue. Petya is back – and this time it’s not just targeting the people with out-of-date software. The list of notable victims already includes Maersk shipping giant, the Chernobyl radiation detection systems, and more. This particular wave of ransomware appears to be aimed at the Ukraine, but the new infection tactics are a clear warning to all computer users that simply staying up-to-date is not a sufficient defense strategy.
We’ve already got you covered
It is already being detected and blocked by Avira. The Avira Protection Services team has picked up three variants of the ransomware during June 27.
“We detected all samples – and we did this without needing to update our machine learning component NightVision.” — Matthias Ollig, Avira CTO
Two paths to your computer
Petya is infecting computers via two primary avenues.
First, Petya has spread by using the EternalBlue vulnerabilities that shot to fame in the WannaCry ransomware. This infection path is primarily a risk for computers that have not installed the patch for this vulnerability. The EternalBlue exploit works both for Internet and LAN connections.
Second, the Trojan collects the locally stored Windows login credentials and misuses them with the PSEXEC tool. This is just a regular tool, usually used by system admins, to run other tools on remote machines they have regular access or logins to. This method works even if the system is fully patched as PSEXEC is not an exploit but a regular tool from Microsoft and SysInternals.
“After decrypting the Trojan completely we also found it not only uses the EternalBlue exploit, but also contains the NSA backdoor DoublePulsar. We are surprised to see that after the WannaCry debacle, there are still so many machines without the latest Windows security updates connected to the internet – especially in critical environments.” — Matthias Ollig, Avira CTO
10 minutes for ransomware
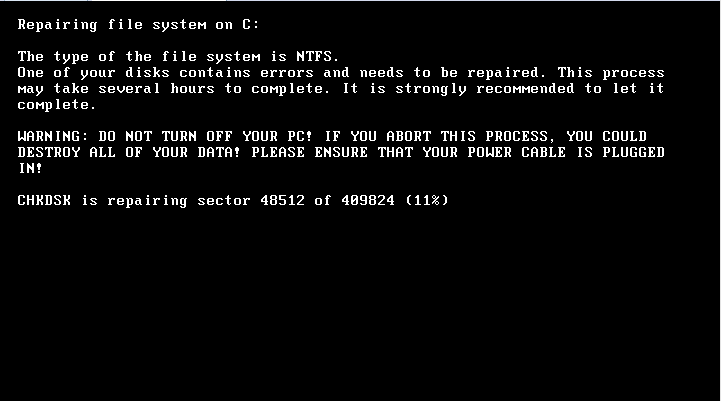
The exploit runs the malware sample via RUNDLL32.EXE as the malware sample is a DLL. The Trojan writes the malicious MBR code and sets up a scheduled task that forces a reboot of the infected machine after 10 minutes. After that, a fake system repair screen is displayed, the screen is attached.
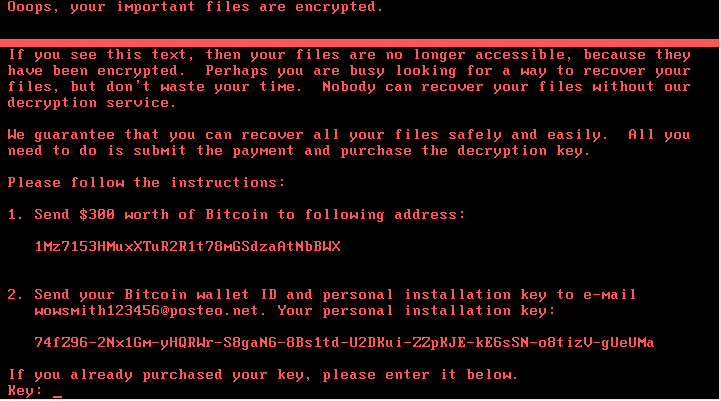
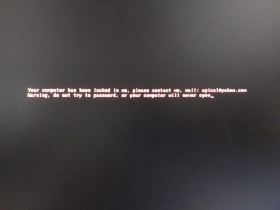
If that is finished, the final lock screen with the red text is displayed.
The unknown connections
The Petya detections have a clear language and operating system concentration. In the Avira cloud detections*, we have noticed the following distribution of the local Windows language setting:
- ru 1,512
- uk 918
- pt 13
- en 7
- de 2
- fr 1
Most users were in either in Russian or Ukrainian language settings – presumably in these locations. However, as this is not the geo-location, it could be users in Ukraine using Russian language setting. Computers impacted by Petya were primarily older Windows systems with Windows 7 and 8. Operating systems:
- Win7 SP1 2,139
- Win7 SPO 181
- Win 8.1 119
- Win Server 2003 14
- Win 8.2 2
The best Petya defense
The first and most important strategy is to have all updates fully installed. As Petya is using a network exploit, the end user does not need to open or click anything – the machine just gets infected without any user interaction.
Updating and patching software is more than a convenience. It is an essential element in online security as the average computer contains a wide range of applications requiring hundreds of updates and patches each year. While some updates are automatic, many require users to search and directly download the needed updates. However, many people are annoyed by popups and unsure of the proper update regime, so they do not update regularly –– and this puts them and their computers at risk. Given this substantial vulnerability, Avira offers a free version Software Updater to enhance user security and its premium Software Updater Pro to put the entire update process on automatic pilot.
Independent testing authority AV-Comparatives has awarded our Avira Antivirus Pro its highest “Product of the Year” award recently this year. Antivirus Pro won the renowned testing laboratory’s top Advanced+ score in all seven specialized tests conducted throughout 2016, leaving other products trailing. The award proves that Avira Antivirus Pro offers the best-possible protection against online threats such as malicious websites, ransomware, Trojans, spyware, and other types of malware.
* All detection stats are from 27.06.2017