Avira researchers have identified vulnerabilities in the Cacagoo IP camera, only a short while after finding that the Victure PC530, wireless security camera posed a threat to users, allowing cyber-criminals to remotely access the camera and view user’s homes.
IP cameras are often found in smart homes and offices, ironically, with the express purpose of enhancing security, Avira’s research labs monitor IP cameras looking for flaws and vulnerabilities, irrespective of company or vendor. During our assessment of different IoT devices, we found vulnerabilities in Cacagoos IP camera that not only enable attackers to intercept and view recorded videos, but also to manipulate the device and other devices within the same network.
We conduct this research and inform vendors about findings so that they can be patched on time, protecting users and products from compromise. This article describes the technical issues behind the vulnerability.
Issues found
- The Telnet service is exploited by a brute-force password attack i.e (login: root pass: cxlinux) – CVE-2020-6852
- Weak authentication of the RTSP service has been uncovered (no password required) – CVE-2020-9349
- A suspicious behaviour has been detected of posting data to a random Chinese domain
Device Specification: Cacagoo IP camera
Device Name: CACAGOO Cloud Storage Intelligent Camera
Model: TV-288ZD-2MP
Manufacture: Shenzhen TOMTOP Technology Co., Ltd.
Firmware Version: 3.4.2.0919
Application: YCC365 plus
Application Version: 3.1042.9.8733
Manufacturer Mailing Address: G-4 Zone 5/F, No.1 Exchange Square, Huanan City, Pinghu Town Longgang District, Shenzhen, Guangdong, China
Email Address: support@cacagoo.com
Importer name: FISHING KING, SLU
Importer Address: PIEDRABUENA,4,4B, MADRID,28026 Spain
Exploiting the telnet service
In order to see which services are being run in the device, we use nmap (i.e nmap -sV <device_ip>). We observe that telnet, HTTP and RTSP services are running.
We tried to access the telnet session by a brute-force attack through a Metasploit module against the custom user-password list and we successfully managed to login to the telnet session with root privileges. Here are the screenshots below:


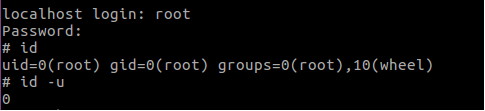
Penetrating and Exploiting other systems in the network using the camera
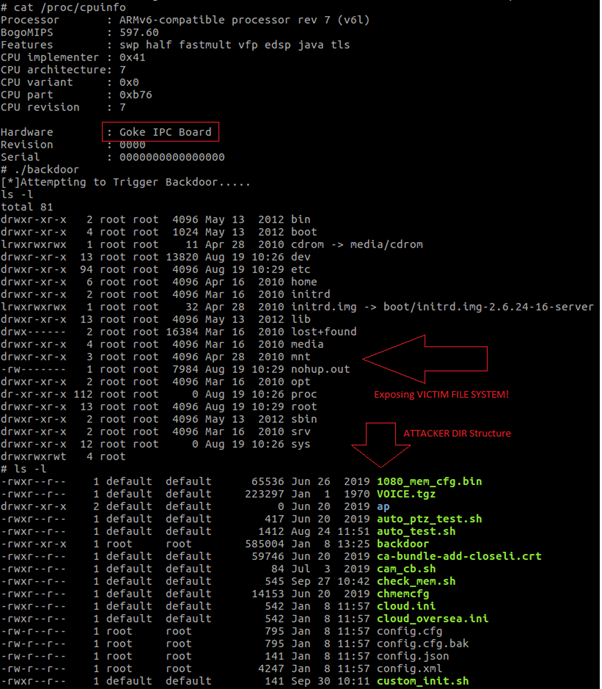
We observed that ftpget is available in the camera and an attacker can use it to download and install any malware, or place a backdoor after having telnet access. To replicate the real-world attack scenario, we placed a backdoor in the camera which can further penetrate the network to scan for other accessible or vulnerable systems and exploit them. Attackers can send commands to these systems and use these cameras as CnC.
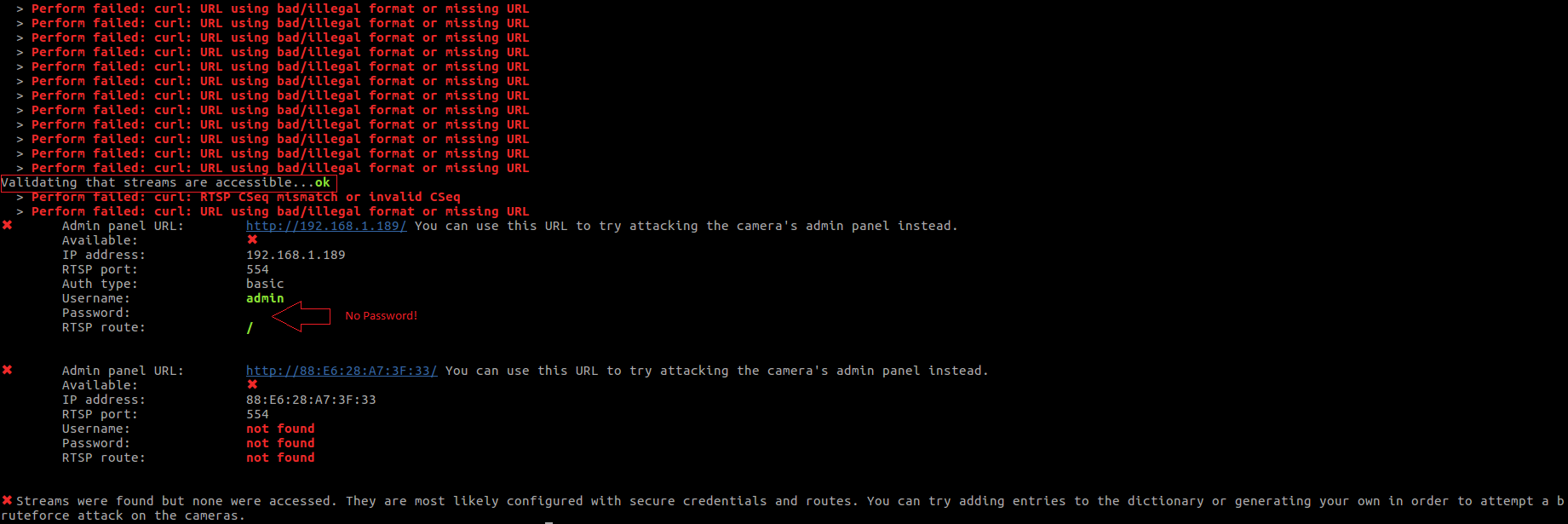
Weak authentication of the RTSP service of the camera (no password required)
We observed that the RTSP service is running at port 554 and 8001. We ran our locally setup tool arsenal to fetch RTSP credentials and route. After running the tools, we noticed a blank username password field. Browsing the RTSP in VLC was the next test to see if we had live video streaming. We opened the VLC and browsed rtsp://192.168.1.189:8001/
We encountered an RTSP authentication POP-UP message, entering admin as the username while keeping the Password field empty. To our surprise, there was LIVE video streaming We recorded the packet streams to get the packets that were being transferred. The screen shots below show the output and authentication before sending the RTSP packets.

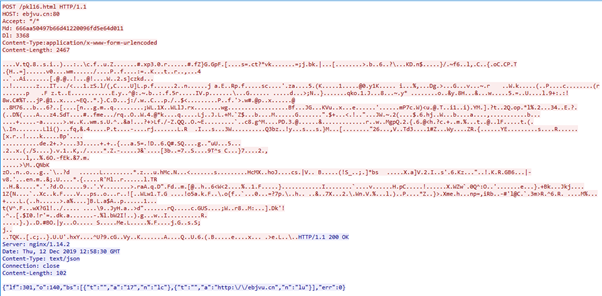
By looking at the traffic, it is visible that the authentication is weak. “YWRTAW46” is a base64 encoded format of username: password. Weak Authentication in the RTSP protocol is indeed a security flaw as an intruder can capture sensitive video/audio by exploiting it.
Unencrypted audio/video in the camera network traffic
Video and audio traffic is also unencrypted as seen below. Besides weak RTSP authentication, traffic should be encrypted or use SRTSP so that if an intruder captured the audio/video traffic, they would not be able to see the stream.

Suspicious behaviour detected whereby the camera posted random data to a Chinese domain
During our network behavioural analysis of both devices, we observed suspicious behaviour while analysing the YCC365 plus application traffic, which really caught our attention. The traffic is below:
Domain is resolved to 112.65.70.245. It is noted that the app is trying to connect to a random Chinese domain (ebjvu[.]cn) on that IP. The info is being leaked through the app, which is suspicious and can be considered as a security flaw.
Conclusion:
As the research shows, there are some serious security issues with these devices and its web interface. It is mandatory to fix these issues to improve the security before they get into the wrong hands. Here are some recommendations from our side:
- Close the telnet service as the open telnet is vulnerable to brute-force attacks.
- Fix weak authenticated RTSP access.
- Establish a strong password to avoid attackers getting access to live video feed.
- Sending data to a random website needs to be blocked.
Last but not least, the lack of sufficient cybersecurity implementations in IoT devices is the next thing to tackle, not only for the IP surveillance industry but for all IoT-based businesses. Learn more about creating a secure IoT environment for customers.














Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.